Relationships Power Application Security in the Cloud. Context Turbocharges It!

Modern cloud services are rich in security controls – offering a vast array of policy enforcement options, access log data, IAM permissions, and other advanced features delivered in software as applications are instantiated. However, in order to benefit from these rich security controls you need to configure the policies to make them effective – and that requires an understanding of your applications and their relationships.
Modern Cloud Environment Challenges
Modern cloud environments can make it very difficult to achieve understanding of applications and relationships – they are often geographically dispersed, frequently changing, diverse, and managed through multiple interfaces by many individuals. It is therefore very difficult to understand what is happening, and what has happened across your application’s lifecycle and therefore how policies should be configured to protect your business.
And this is a problem. If you look at some of the high profile cloud breaches over the past few years, they have been primarily caused by a failure of policy or configuration to protect the applications and data executing within a cloud with a seemingly rich array of security capabilities.
This leads us to an important concept within cloud security known as the Shared Responsibility Model, which describes the role of the cloud provider and the role of the customer. In short, the Shared Responsibility Model states that the provider is responsible for the security of the cloud, and the customer is responsible for the responsibility of the applications in the cloud. In particular, this includes designing and managing the policies to protect those applications.
This is where the vArmour Application Controller and its Security Graph come in.
The Application Controller is an advanced risk and policy engine, designed to address this problem no matter where your applications live – within your private data center, a private cloud or across multiple public cloud environments. Increasingly, enterprises have dependency on more than one environment, which is why the Application Controller abstracts their differences – focusing the operator on the application itself and the policies necessary to provide effective security.
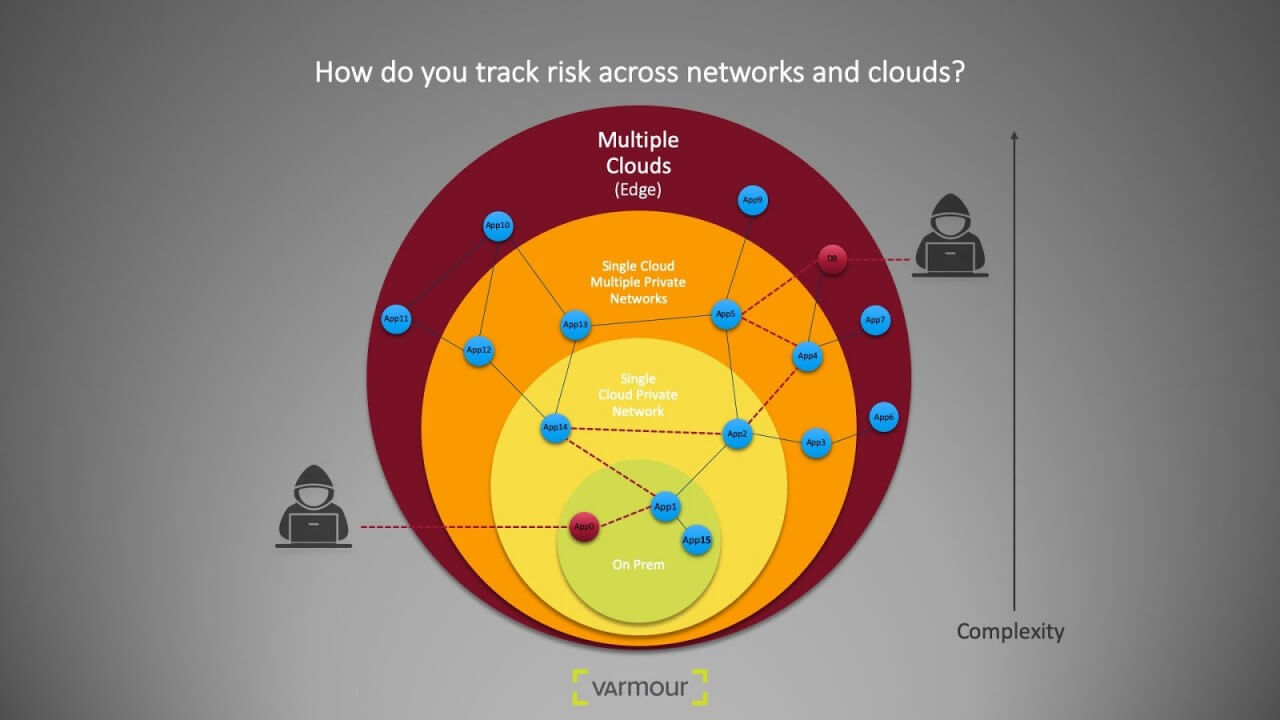
In this example, an attacker may leverage access to workload “App0” and exploits relationships to gain access to critical asset “DB.” vArmour Application Controller can quickly identify this type risk among the thousands of relationships in your multi-cloud environment.
Security Graph Simplifies Security
At its heart, the Application Controller uses the Security Graph to record every node and relationship within your multi-cloud environment, using advanced analytics and Machine Learning (ML) to organize the information in an application and risk-centric fashion in order to ease the path to simple, effective security policies. In environments with thousands of workloads you will quite possibly see millions of relationships, and the ability to organize this information is crucial in making security simple and effective – as opposed to dumping a complex spaghetti graph in front of the operator, leading to the problem described by Bruce Schneier “Complexity is the worst enemy of Security”.
So, how does vArmour accomplish this? Firstly, the Application Controller uses advanced ML and other analytical models to classify and organize nodes and their relationships – to identify application functions, to group functions together where affinity is found, and to organize nodes and their relationships into application stacks that a DevOps or security professional will find easy to identify.
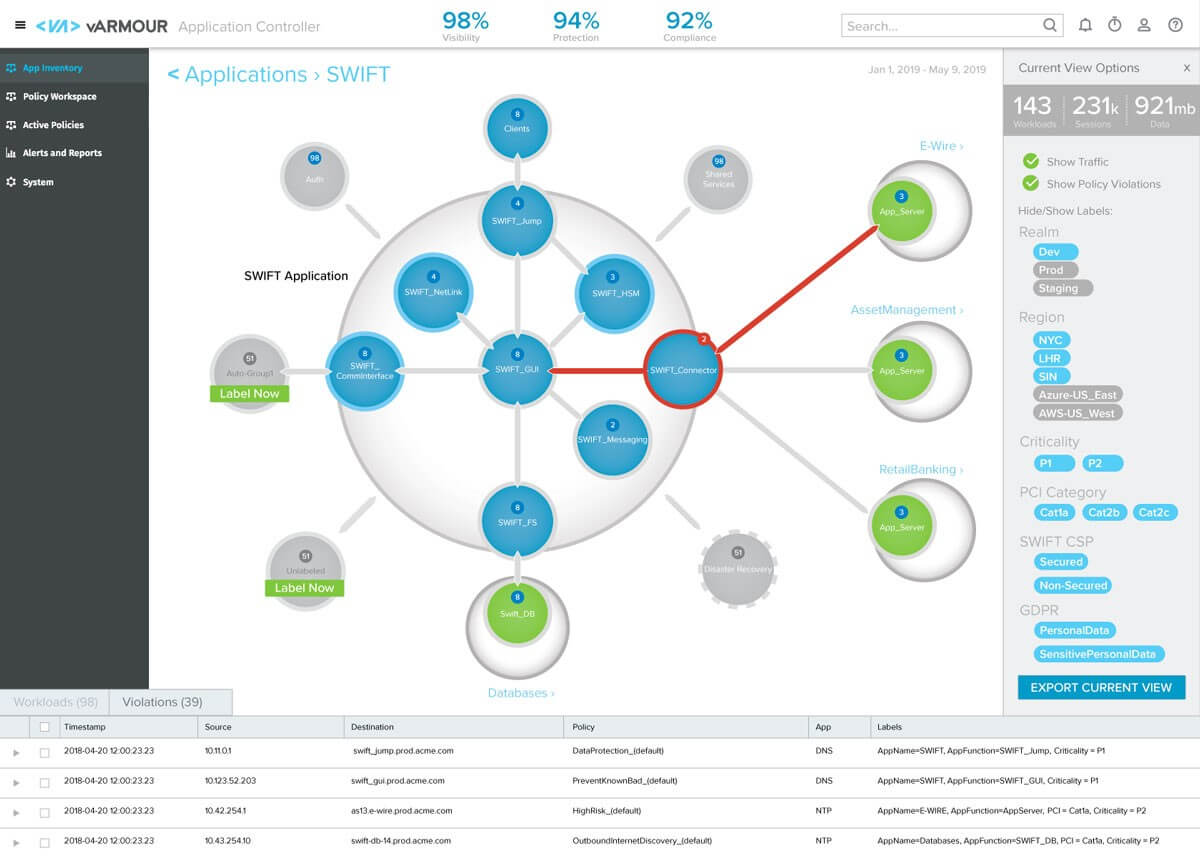
Visualize your Security Graph with the vArmour Application Controller
Relationships Matter: vArmour Sees and Protects your Applications
In order to take this first step, you need to have a deep and rich understanding of relationships. As we always say in cloud security, “Relationships Matter”.
Security Graph technology provides you with the insights you need to achieve the application security you require, and also provides you with the model to understand so much more about risks to your applications and your business.
Application Controller allows you to choose the applications you want to protect and select the way in which you want to protect them. Unlike simplistic policy systems that focus on turning individual connections into whitelist rules, Application Controller allows you to declare a security intent – for example, the separation of domains, the isolation of an enclave or the application of a compliance mandate such as a PCI DSS compliant segmentation policy. Because the Security Graph understands all the relationships and plenty of other context in addition, it is able to fulfill a requirement to apply those PCI segmentation controls to every in-scope PCI asset which has been recognized within Security graph.
Once the Application Controller has modeled your candidate policies within the Security Graph, it will evaluate them against historical behavior and the capabilities of the cloud environments, deploy them and ensure they continue to remain deployed and effective. This assures continuous compliance of your applications to your security intent.
Application Controller takes you from no visibility to providing you with powerful insight into your application environment. Application Controller then ensures your policies are effectively deployed in order to meet your responsibilities under the Shared Responsibility Model for cloud security.
Security Graph Helps you Achieve the ‘Network Effect’
Our customers are also telling us that the Security Graph has many more applications than providing application discovery and policy management. Relationships matter throughout security and by adding more relevant information into the graph, you achieve a ‘network effect’ to improve your security posture, reduce your attack surface and understand potential blast radius.
This assembly of context has enabled our customers to become incredibly innovative in all sorts of ways, including:
- Validating inventory. Because the Application Controller understands relationships, it can classify systems by their behavior which enables inventory validation and improves the data quality within CMDBs. Accurate inventory is a prerequisite to any assessment of risk and control requirements.
- Understanding dependencies. Once you understand relationships, you can assess dependencies. From both a risk and operational standpoint, it is incredibly valuable to gain context about systems and services upon which your critical business functions depend.
- Providing context to vulnerability and risk assessments. Vulnerabilities in complex software systems are a fact of life, and often a very time-consuming task to address. By inserting vulnerability information into the graph, you can understand the potential impact on critical business applications and functions. This context allows more effective risk management through prioritization and also access to additional insights such as how security policies might help to protect vulnerable systems and the business functions that depend upon them.
SDK Further Expands the Security Graph ‘Network Effect’
This centrality of the Security Graph that results in effective risk-driven cloud security leads us to the SDK we have also launched with Application Controller release 5. The SDK extends the core principle of leveraging the investments customers already have made in their environments.
Alongside our numerous cloud integrations, the SDK provides our customers and partners with a streamlined opportunity to benefit from the Security Graph ‘network effect’ by integrating data from disparate sources, telemetry sources, control plane metadata, inventories, directories and other security systems.
If you have ideas to integrate your third-party data into the Security Graph, the SDK makes it easy.
I would also love to hear about your ideas for Security Graph integrations, and how you might benefit from this revolution in security risk management (please get in touch at marc@varmour.com).
To see for yourself what Application Controller can do for you, download the free trial.
To learn more about our SDK integration capabilities, view our AWS and NSX videos below, or go to the vArmour Youtube channel to view ones on Azure, Tanium, and more.




