What the Financial Services and Markets Act means for Technology Resilience

The Monetary Authority of Singapore’s “Financial Services and Markets Act 2022” demands Technology Resilience – what does that mean and how can you achieve it?
In June 2022, the Singaporean parliament passed the Financial Services and Markets Act (FSMA) 2022 in order to enhance financial sector-wide supervision and address new and under-addressed areas of risk with a view to improving the resilience and integrity of the sector. A key component of this legislation includes the requirement for improved and formalized Technology Risk Management (TRM) practices defined within guidelines produced by the Monetary Authority of Singapore (MAS) in order to improve Operational Resilience across the sector. Failure to meet the requirements defined within the Business Continuity Management (BCM) and TRM guidelines will result in fines of up to $1,000,000 (with an additional $100,000-per-day of continuing violation) from Summer 2024 when audits will commence.
The requirements outlined within the BCM Guidelines (and sections of the TRM control requirements) are broadly consistent with the global best practices as established by the FFIEC and OCC (in the United States), the European Union’s DORA requirements, and the APRA CPS 230 guidelines (in Australia). In this blog we will explore the MAS guidelines and describe how they can be addressed in an automated manner, providing consistency across organizations that might also need to address requirements within the USA, Australia, UK or Europe.
Why Now?
MAS is concerned with the stability of each financial institution and soundness of the financial system as a whole, in particular how it might be affected by operational failures relating to digital services cascading across the high degrees of interconnectedness resulting in broader contagion and instability across the entire sector.
Like other regulators, MAS has responded to the increasing complexity and associated operational risks associated with the highly digitalized and fast moving financial services sector and they are demanding improved governance and management of risk that might emerge in real time.
An analogy I like to use to describe this approach is the importance of the ‘heads up display’ (HUD) in modern fighter aircraft—in order to reach extraordinary speeds and make split second decisions, it is critically important to utilise accurate, relevant information which offers the opportunity to take timely or (in many cases) immediate corrective action when required. And for sure, that HUD along with every other critical function within the aircraft must be resilient and reliable. So, in order to go faster (in the case of financial services organizations, to innovate and offer compelling new products) you need to have the correct information to exert appropriate control and make effective operational and cyber decisions in a highly dynamic environment without ‘stopping the aircraft’.
Regulators and governments (in this case MAS as directed by the Singaporean government’s legislation) are responding to the critical nature of their financial systems within the modern digital economy, and also reacting to a number of significant operational failures which have caused disruption to citizens, businesses, and overall economic confidence.
Within Singapore, in particular, we have clearly seen the result of operational issues related to digital complexity impact DBS bank where a series of failures and disruptions have had a material impact on their customers (including a 2-day disruption to customers accessing their accounts in 2021, and several more major issues in the past year) and resulted in an order from MAS to set aside an additional S$1.6 billion in regulatory capital. Once the Financial Services and Markets Act passes into law, the intent is that the processes and tools put in place will remediate many of the issues experienced by consumers – and the penalties levied against non-compliant institutions will become even more severe.
What is Required and How do I achieve this?
MAS’s approach to Digital Operational Resilience / Technology Risk Management has many similarities to best practices defined elsewhere within the world, and many of the techniques to address the requirements will be globally consistent.
However, MAS does call out some particularly important and specific requirements as outlined below.
MAS Business Continuity Management Guidelines
Establishing Critical Business Services and Functions
Business Services are consumed by customers and are therefore the entity that needs to be assessed and protected in terms of risk, resilience and recovery capability. In addition, other business services are required to participate within markets and ensure the liquidity and stability of the institution and the broader economy within which it participates.
However, within complex digital environments, those services are usually delivered utilising a complex collection of functions which interact to provide the service, and also consume data and services from other functions upon which they are dependent.
By recognizing the complexity and the inter-relationship between the institution’s critical services, their requirements for resilience (in terms of impact and risk tolerance), and the functions upon which they depend, MAS has created a taxonomy for organizations to model and understand their critical systems and processes. This approach is described within section 2 of the BCM guidelines.
Within Section 3, MAS expands this concept to communicate the importance of ensuring consistency between the service impact tolerance (SRTO) of critical services and the functions and dependencies required for its delivery.
vArmour Relationship Cloud utilises this precise approach to assist organization in identifying and assessing the relationships between business services and functions, and provides the capabilities to automatically map properties such as Recovery Time Objectives in order to dynamically identify where risk or impact tolerances might be violated.
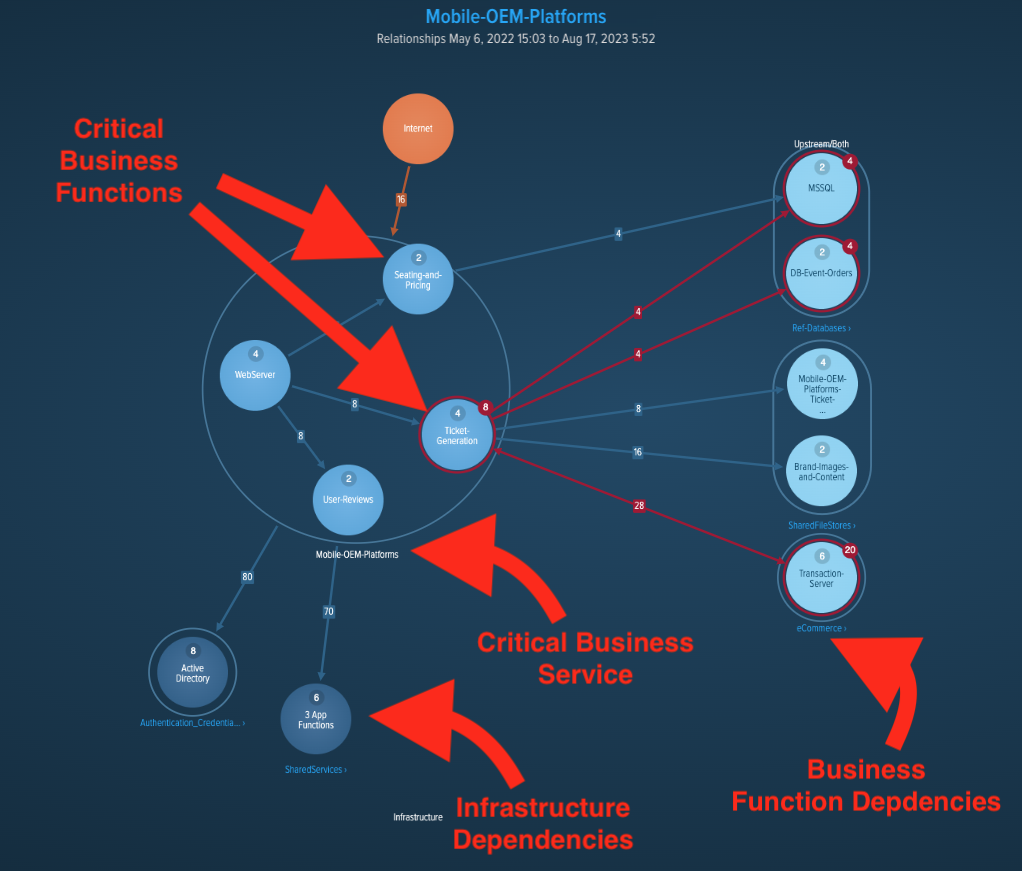
Figure 1: Business Services, Business Functions, and other Dependencies
Dependency Mapping
MAS explicitly identifies and prescribes the need to map dependencies in order to establish the scope of Critical Business Service as the basis of all subsequent attempts to manage risk. In calling this out, MAS correctly recognizes the importance of accurate information as the basis for the Technology Risk Management process.
Section 4 of the BCM Guidelines states:
“The financial sector has become increasingly interconnected with the growing reliance on common IT systems and third parties. As a first step to mitigate the risks arising from these linkages, the FI should identify and map the end-to-end dependencies covering people, processes, technology and other resources (including those involving third parties) that support each critical business service.
The dependency mapping will enable the FI to identify resources critical to the service delivery, consider the implications of their unavailability, and address any gaps that could hinder the effectiveness and safe recovery of the critical business services. The FI should use the information derived from the dependency map to verify that the recovery of the business functions and their dependencies can meet the established SRTOs.”
At vArmour we fundamentally believe that the accurate, data driven dependency map must form the basis of an effective technology risk management process. By enriching the graph with metadata from the customer’s environment, we can produce maps that recognize relationships between RTOs, people, locations (for example, failure domains and restricted zones), third parties, and other significant factors. By establishing the Map of Business Services and Functions, we can empower service owners and risk managers to execute their responsibilities simply and effectively.
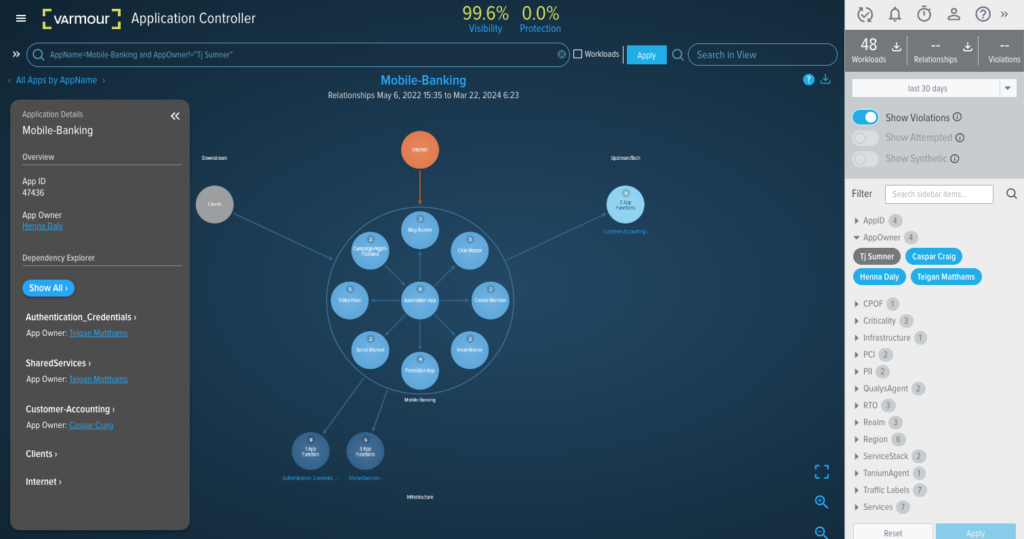
Figure 2: Business Service Dependencies filtered upon owner
Concentration Risk, Continuous Review, and Testing
The next critical requirements identified by MAS depend largely upon accurate information identified within the Dependency Map. The Map enables an organization to address the next few sections by asking questions like:
- What is my Critical Business Service dependency on provider X? (provider concentration risk)
- What is my Critical Business Service dependency on Datacenter Y? (technical resilience and concentration risk)
- What function owners assume the largest amount of dependency risk? (personnel concentration risk)
- What would the impact be of Severe but Plausible Incident Z? (Continuous Risk Assessment / Review, Testing)
- Which Critical Business Services would be impacted were vulnerability A to be exploited? (Continuous Risk Assessment / Review, Testing)
- Where are my SRTO / RTO mapping risks? (Testing)
The vArmour Map forms the basis of an accurate assessment of Impact and Risk against the organizations defined tolerances, and facilitates streamlined scenario testing based upon accurate and up to date information without the requirement for lengthy discovery programs.
Furthermore, the use of the vArmour Rules Engine can enable organizations to encode impact and risk tolerances so that when drift and change within the environment results in new threats to operational resilience, alerts can be issued to Business Service owners for immediate triage and mitigation.
So you don’t need to wait for a periodic risk assessment, BIA, or scenario test to identify the threats to your Critical Business Services.
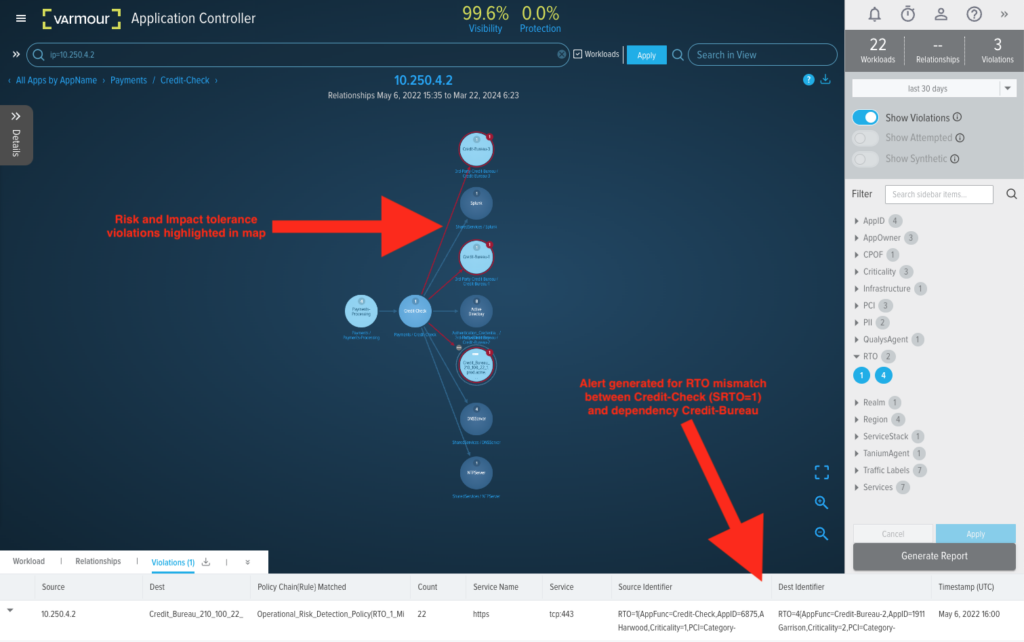
Figure 3: SRTO Alert defined within the vArmour Rules Engine fired by RTO inconsistency
MAS Technology Risk Management Guidelines
In addition to the BCM guidelines, MAS has produced a broad set of requirements to reduce technology risk, “Technology Risk Management Guidelines” which are also enforced under the ‘Financial Services and Markets Act’. These guidelines are broad and encompass areas such as secure development practices, physical datacenter protection, access management, cryptography, and security across networks, systems, IoT and web applications. There is also quite an overlap with the aspects of the BCM guidelines.
However, there are two distinct areas where accurate information and situational awareness about the operational environment are absolutely critical;
Change Management
A key pillar of Operational Resilience is the effectiveness of change management (Section 7.5.1), in particular in planning, reviewing, approving, co-ordinating and testing changes. The Map is a key factor in this work, enabling organizations to plan changes effectively based upon accurate service, function and dependency understanding. It is also utilised by many organizations to simulate the impact of a proposed change utilising a digital twin of the production environment.
Baselining and Anomaly Detection
Anomaly detection is used by many complex organizations to proactively identify deviations from normal behaviour which might represent an operational or cyber risk. MAS are explicit in their requirements for the generation of a baseline which is regularly evaluated against observed activity within Section 12.2.3;
“To facilitate identification of anomalies, the FI should establish a baseline profile of each IT system’s routine activities and analyse the system activities against the baseline profiles. The profiles should be regularly reviewed and updated.”
vArmour Relationship Cloud enables organizations to automatically establish a baseline profile at the system, function or service level which is continuously evaluated against observed activity in real time, generating alerts where material deviations are identified. Once again, the dependency map enables institutions to take a proactive approach to operational resilience without expensive and inaccurate manual intervention, in order to meet their obligations under the Financial Services and Markets Act.
Summary
Like many regulators around the world, the Monetary Authority of Singapore have recognized the criticality of Operational Resilience to the stability and health of the Financial System and broader economy. They have put in place detailed and constructive guidance establishing best practice within this space.
vArmour’s Relationship Cloud provides institutions with the ability to streamline and automate their discovery, mapping, impact assessment and risk management processes required to become and remain compliant. Going further, Relationship Cloud enables organizations to eliminate the operational costs associated with manual discovery and assessment, reduce errors caused by outdated information and human error, and move to a world where risk management occurs on a continuous basis aligned with the speed of business change and innovation.
Operational Resilience can be a strategic differentiator and provides real benefit to an institution’s customers and stakeholders. vArmour Relationship Cloud embeds that differentiation into the fabric of your institution.
Request a demo here to see firsthand how vArmour Relationship Cloud streamlines your journey to MAS requirements and technology resilience.




