Addressing the DORA ICT Risk Management Requirements

Effective ICT Risk Management provides an organization the basis upon which they can realize Digital Operational Resilience. It provides organizations with the ground truth knowledge they need to anticipate and avoid incidents, recover from incidents when they occur, and effectively manage their digital risks in order to proactively prevent risks from contributing to future incidents. ICT Risk Management also provides organizations with the information they need to effectively transform, adopt new digital architectures, and adopt security best practices such as Zero Trust.
In our previous article, we provided some background information on the importance of Operational Resilience within digital organizations, its history and the common requirements. This article will dive deeply into the specific requirements to become operationally resilient by effectively managing cyber and ICT Risk. ICT Risk Management is a core pillar of all Operational Resilience requirements and standards, and is particularly called out as a fundamental pillar of the European Digital Operations Resilience Act (DORA).
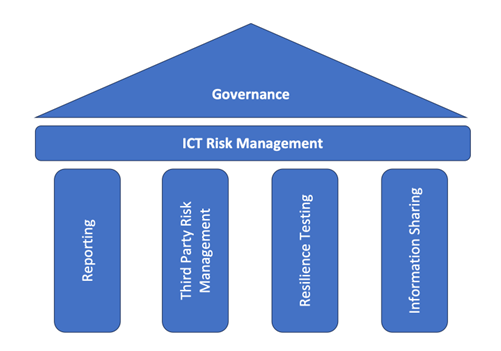
Figure 1. The Pillars of DORA
The Workflow for ICT Risk Management
Through the detailed DORA articles 5-16, the European Union defines a set of prescriptive requirements which essentially lay out a process for the delivery of an effective ICT Risk Management program. These requirements are common across other global Operational Resilience guidelines and regulations, but DORA defines those requirements in granular detail so we will use that as a guide.
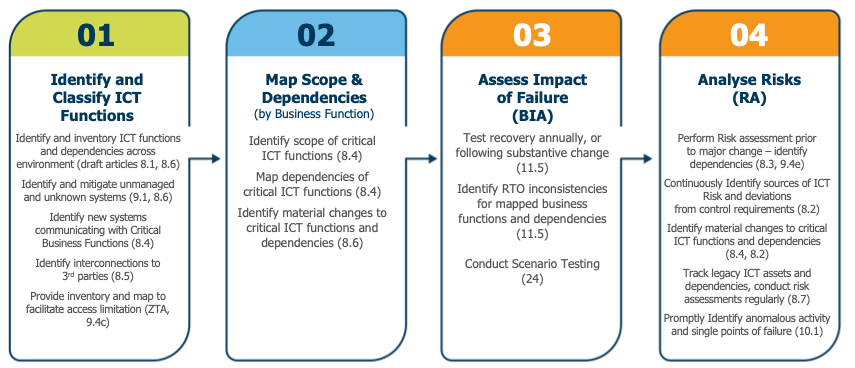
Figure 2: The steps in the ICT Risk Management workflow as defined by the DORA articles (including brief summaries)
The next 3 articles in this blog series will dive into each stage of the workflow, demonstrating how this can be automated and simplified, but let’s take a moment to consider each stage and how they build upon each other.
Stage One – Identifying and Classifying ICT Functions
Risk Management is fundamentally based upon the assessment of information. If you don’t have the information you need, your risk assessment cannot be complete or effective (unless you are able to accept the known risks associated with incomplete information). So, DORA begins its ICT Risk Management journey in article 8 with identification, classification and documentation of all business functions and ICT assets supporting those functions. This enables organizations to identify risks (cyber and otherwise) and to also accurately understand the scope and dependencies of business functions in order to meet the requirements at later stages of the workflow. The inventories and maps produced (as dependencies are part of the base inventory requirement in a highly interconnected digital ecosystem) must be updated periodically, and every time any major change occurs. In fast moving, highly automated digital environments this information needs to be acquired and updated automatically so that innovation isn’t disrupted or information missed causing blind spots.
Stage Two – Map the Scope and Dependencies of your Business Functions
Once the information has been acquired, organizations may focus on their Critical Business Functions and Important Business Services in terms of delivering Digital Operational Resilience. This stage of the workflow involves identifying the map of interdependent systems required to deliver a business function, and to identify when material changes occur (which might impact the BIA or Risk Assessments associated with that function). Many organizations spend hundreds of hours assembling this information each year using laborious processes involving scripts, spreadsheets, and consultants which results in immediately outdated, incomplete results which form the basis of many organization’s operational challenges. At vArmour we believe you should use software to automate this process and provide you with the complete ground truth about your business functions and associated risks at all times.
Stage Three – Assessing the Impact of Failure (the Business Impact Analysis)
Once you understand the material components (people, processes, assets and services) required to deliver a business function then you can conduct your Business Impact Analysis (BIA). Whereas the BIA historically focused upon disaster recovery scenarios (floods, civil unrest, power outages, telecom failures), modern Ops Res requirements focus also upon a broad(er) range of severe but plausible scenarios, including the failure of an interdependent system or service which might not have been well understood previously. The basis of a comprehensive and accurate map enables organizations to execute their BIAs and scenario testing effectively utilising reliable ground truth intelligence. Furthermore, the use of an automated Risk Engine can enable organizations to understand immediately their Impact Tolerances are violated in complex, fast changing environments.
Stage Four – Continuously Assessing your Risks (the Risk Assessment)
If Operational Resilience is about going beyond recovery planning (which it most definitely is!), then the Risk Assessment is the place where organizations can proactively take the steps necessary to identify, assess and mitigate risks before they turn into incidents. The vArmour Decision Intelligence Map enables organizations to carefully assess and plan operational change with a full understanding of asset, service and application interdependencies and to identify where interdependency risk changes. Additionally the vArmour Risk Engine enables organizations to define the technical risk tolerances for their Critical Business Functions to identify where a condition has occurred which breaches enterprise policies and must be mitigated. In complex, fast changing and highly interconnected environments it is impossible to meet the continuous risk management demands of DORA without using an automated approach based upon continuously updated information. vArmour Relationship Cloud enables organizations to become proactive in their risk management practices, even in the most complex digital environments.
What’s Next
Over the next 3 articles / coming 3 weeks we will deep dive into the DORA article specifics for ICT Risk Management, assess their implications, and demonstrate the automated approach that vArmour Relationship Cloud takes to deliver on those requirements.
Schedule:
- Week of Nov 27 – Stage One – Identifying and Classifying ICT Functions
- Week of Dec 4 – Stage Two – Map the Scope and Dependencies of your Business Functions
- Week of Dec 11 – Stages Three and Four – Executing the BIA and continuously assessing your risks (the Risk Assessment)
DORA is carefully designed to require organizations to embed Risk Management into their Digital Operations. As we will see over the next few weeks, the vArmour Decision Intelligence Platform delivered by Relationship Cloud enables organizations to adopt Operational Resilience as a strategic differentiator without disrupting their entire operational model or increasing costs.
Decoding DORA Video:
Automating ICT Risk Management for Operational Resilience | Decoding Dora Part 1 of 4




