Decoding DORA ICT Risk Management Requirements: Step 1 - Identifying and Classifying ICT Functions

Table of Contents
- Operational Resilience and ICT Risk Management in DORA
- Understanding Step One: Identifying and Classifying ICT Functions
The Value Provided at Step One
- Outcomes of Identifying and Classifying ICT Functions
- Challenges with CMDBs and Static Inventories
- Requirement 1: Identify, Classify, and Inventory ICT Functions and Dependencies
- Requirement 2: Identify and Mitigate Unmanaged and Unknown Systems
- Requirement 3: Identify New Systems Communicating with Critical Business Functions
- Requirement 4: Identify Interconnections with Third Parties
- Requirement 5: Provide an Inventory and Map for Access Control
Conclusion – It’s all about situational awareness
- vArmour Relationship Cloud and ICT Risk Management
- Next Steps in the ICT Risk Management Process
Introduction
So far in this series we’ve explored Operational Resilience, and broken down the workflow for effective ICT Risk Management, which is one of the key pillars of DORA (and other global regulations, including those defined by OCC, FFIEC BCM, ASIC, and MAS).
Today, we’ll deep dive into the first step in that workflow — Identifying and Classifying ICT Functions and their interdependencies. Specifically, we’ll assess the specific requirements defined within the articles, the intention and value of this step, and also provide a demonstration of how this requirement can be automated and simplified.
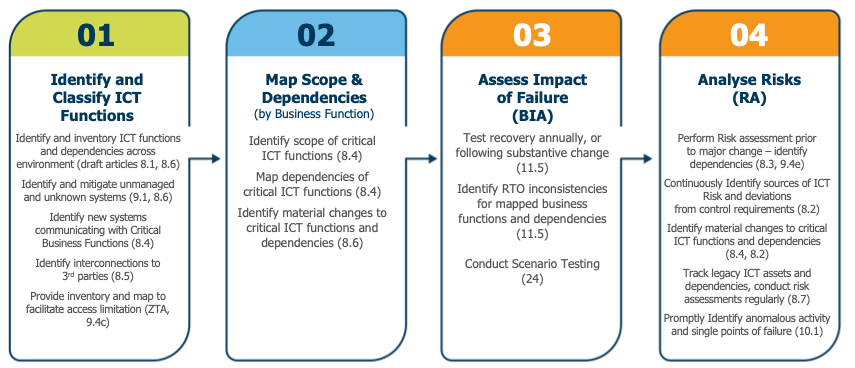
Figure 1: The steps in the ICT Risk Management workflow as defined by the DORA articles (including brief summaries)
The Value Provided at Step One
All aspects of effective risk management depend upon accurate information. By identifying and classifying ICT functions and their interdependencies, you can achieve the following outcomes:
- Identifying systems which might present risk (cyber or operational) to the environment.
- Identifying all systems that are required to deliver a business function.
- Providing the baseline knowledge required to reduce access and employ cyber protection of business functions.
CMDBs and other static inventories can provide a starting point for this work, but have two fundamental challenges:
- CMDBs rarely have the complete picture of an environment which leads to blind spots. A system which provides dynamic discovery is required to identify new or incorrectly managed systems and validate/reconcile any information stored within static inventories.
- CMDBs have a limited understanding of application and infrastructure dependencies and no ability to identify when new dependencies occur.
The DORA Requirements
Requirement 1: Identify, Classify and Inventory ICT Functions and Dependencies Across the Environment
Article 8.1
As part of the ICT risk management framework referred to in Article 6(1), financial entities shall identify, classify and adequately document all ICT supported business functions, roles and responsibilities, the information assets and ICT assets supporting those functions, and their roles and dependencies in relation to ICT risk.
Article 8.2
Financial entities shall, on a continuous basis, identify all sources of ICT risk, in particular the risk exposure to and from other financial entities, and assess cyber threats and ICT vulnerabilities relevant to their ICT supported business functions, information assets and ICT assets.
Article 8.6
For the purposes of paragraphs 1, 4 and 5, financial entities shall maintain relevant inventories and update them periodically and every time any major change as referred to in paragraph 3 occurs.
ICT Risk Management starts with information. DORA requires organizations to have the capability to identify and classify all ICT systems for the purposes of identifying the resources necessary to deliver business functions (8.1) and identify sources of ICT and cyber risk (8.2).
The articles require regular updates (8.6) to this inventory, which for dynamic cloud-based entities must be extremely frequent, particularly for the purposes of continuously identifying sources of risk (as defined in article 8.2)
These requirements will be challenging for organizations relying on CMDBs alone to address them, as they often lack a holistic and up-to-date view of dynamic environments, which can make their data unreliable. Reconciling CMDB data manually, as many attempt to do, is a time consuming, costly, and similarly error-prone effort.
In contrast, the vArmour Relationship Cloud tackles these shortcomings head-on. By ingesting all customer telemetry from cloud, network, existing workload agents, and inventory APIs within the environment, the Relationship Cloud ensures full coverage and immediate identification of systems as soon as they appear anywhere on the customer network. Relationship Cloud’s classifiers also classify systems based upon observed behavior which can assist in inventory management and data reconciliation.
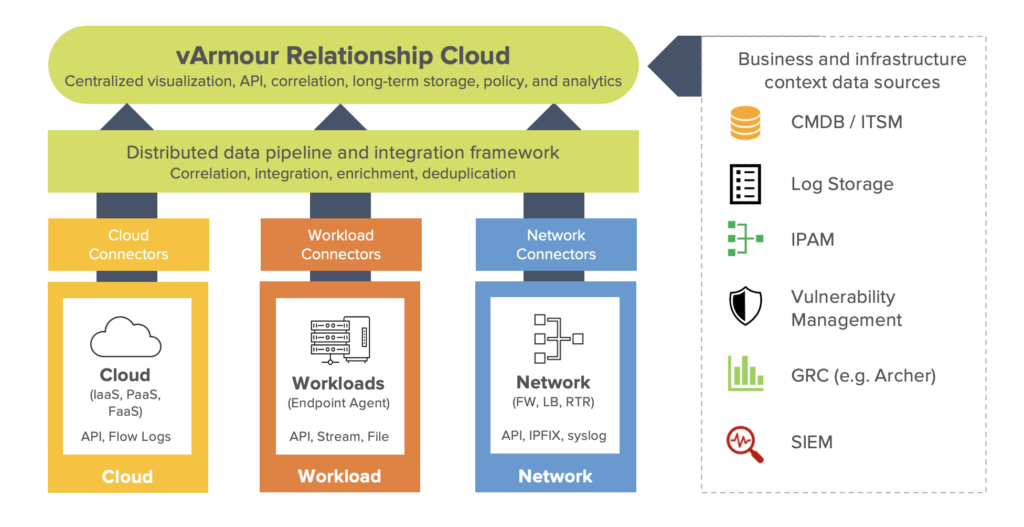
Figure 2: vArmour Relationship Cloud integration framework
Requirement 2: Identify and Mitigate Unmanaged and Unknown Systems
Article 9.1
For the purposes of adequately protecting ICT systems and with a view to organising response measures, financial entities shall continuously monitor and control the security and functioning of ICT systems and tools and shall minimise the impact of ICT risk on ICT systems through the deployment of appropriate ICT security tools, policies and procedures.
DORA requires that all ICT systems within the environment are managed and controlled, and that those controls and procedures are enforced. In order to ensure this outcome, an organization needs a process to continuously monitor for unmanaged and unknown systems which can be a particular source of risk and vulnerability.
The vArmour Relationship Cloud provides an optimized workflow to identify unknown or unmanaged assets, the information required for rapid assessment, and the ability to produce immediate notification where unmanaged systems access specific business functions.
The video accompanying this article demonstrates a highly automated workflow to identify, triage and remediate unknown or unmanaged systems in complex environments.
Requirement 3: Identify New Systems Communicating with Critical Business Functions
Article 8.4
(Financial Entities) shall map the configuration of the information assets and ICT assets and the links and interdependencies between the different information assets and ICT assets.
DORA (and many other regulators) require financial entities to focus in particular on Critical Business Functions and Important Business Services. In particular, organizations are required to manage the operations of business functions in order to address risk appropriately, including ensuring that interdependencies meet operational and cyber requirements and constraints.
The vArmour Relationship Cloud fully maps the dependencies of all business functions, applies policies to ensure risk and impact tolerances are met, and allows organizations to be informed immediately a material new dependency occurs to a business function.
Requirement 4: Identify Interconnections with Third Parties
Article 8.5
Financial entities shall identify and document all processes that are dependent on ICT third-party service providers, and shall identify interconnections with ICT third-party service providers that provide services that support critical or important functions.
Third party risk management is another fundamental pillar of DORA. Many organizations are primarily addressing this through their procurement and vendor management processes. However this approach does not provide observability into the digital interactions of business functions with third party services, including any dependency upon cloud service providers and potentially inappropriate concentration risks. It also fails to identify where third party risk is being assumed through shadow IT, or BU-initiated adoption of third party services.
By observing application and infrastructure activity, the vArmour Relationship Cloud offers organizations the capability of understanding business function behavior that introduces third party risk, which can be used alongside emerging procurement procedures to provide the ‘complete picture’ of third party risk in ICT systems.
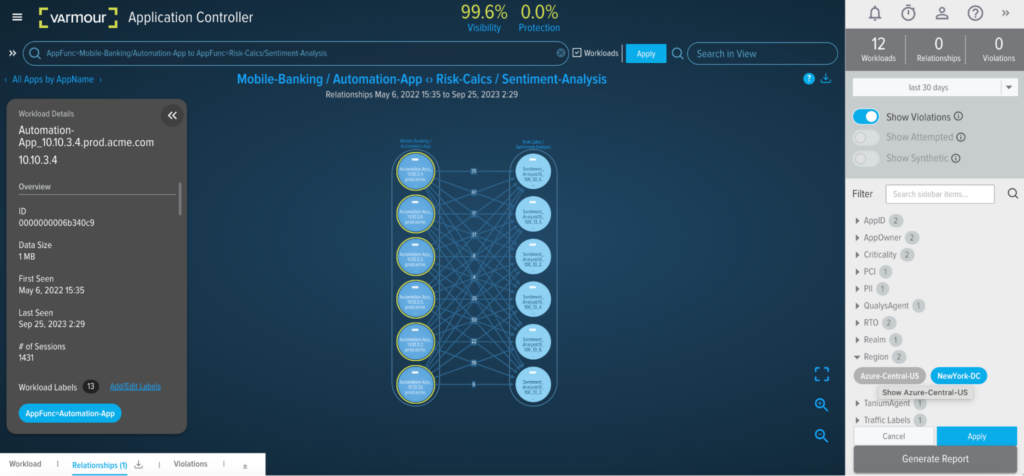
Figure 3: Screenshot of vArmour Relationship Cloud showing a full dependency of the Application Function ‘Mobile Banking / Automation’ on the Azure Central US Datacenter.
Requirement 5: Provide an Inventory and Map to Facilitate Access Control (for example, Zero Trust access controls)
Article 9.4c
Implement policies that limit the physical or logical access to information assets and ICT assets to what is required for legitimate and approved functions and activities only, and establish to that end a set of policies, procedures and controls that address access rights and ensure a sound administration thereof;
As part of the requirement to improve cyber resilience, DORA article 9.4 requires organizations to reduce access to ICT systems, in particular those delivering Critical Business Functions.
The identification and classification of assets and interdependencies is a key requirement for the implementation of Zero Trust or other strategies to reduce access to the ICT assets delivering Critical Business Functions. Without a clear understanding of dependencies and a scope of the assets involved, Zero Trust or segmentation strategies are fragile or insecure and policy management is impossible.
vArmour’s Relationship Cloud enables organizations to obtain the situational awareness of their systems required to adopt safe and secure Zero Trust and segmentation strategies. In addition to this base information, it also enables organizations to simulate the impact of security policies and to design policies using observed behavior within the environment.
Conclusion – It’s All About Situational Awareness
In order to execute an effective risk management program, organizations need reliable information to help them navigate their complex and fast changing digital environments.
Further, DORA now requires organizations to maintain that information to continuously assess their risks and ensure operational and cyber integrity.
By collecting and analyzing telemetry and inventory data across an organization on a continuous basis, the vArmour Relationship Cloud enables them to meet DORA requirements for ICT Risk Management, establish Operational Resilience as a strategic differentiator, and also automates and simplifies the legacy processes organizations use to establish ground truth from their disparate telemetry data sources. We’d be happy to show you this in person. Request a demo here to see how we can help.
Once the entire digital estate is identified and classified, this enables operational and cyber excellence and the accurate execution of Business Impact Analyses and Risk Assessments. We will explore these next steps in the ICT Risk Management process in our upcoming articles in this series.
Video Demo
See how the vArmour Relationship Cloud simplifies the process of identifying and classifying ICT functions and their dependencies to achieve specific DORA requirements here.




