Application Relationship Management: A Pathway to Mitigate Widespread Catastrophic Vulnerability Exploitation (CVE)

The catastrophic remote code execution (RCE) vulnerability “Log4Shell” within Log4j2 has been broadly exploited across the public internet and enterprise environments, enabling attackers to execute privileged shell commands upon vulnerable systems. This ongoing event is a serious threat for several converging reasons:
-
- Severity. The vulnerability enables attackers to remotely execute systems commands from within multiple applications, from Minecraft game messaging to neo4j queries, and web interface input using a simple escape string.
- Function ubiquity. The ubiquity of log4j Apache for logging across all sorts of applications and services, including middleware frameworks, numerous databases, web servers, stream processing functions, and games means that exploitation can be executed across all sorts of vectors, and is very difficult to detect at scale. In a large heterogeneous enterprise environment with many thousands of systems affected, it is difficult for organizations to know where to start.
- Sub-dependencies. Sometimes log4j is deployed as part of an OS build or application, but more often it is a sub-dependency of a library, compiled into a JVM. This means that multiple versions can be resident at once on any system and it can be complex and tricky to unpick. Even worse, sub-dependencies are often dictated by the primary library so remediating can become risky and subject to delays related to the primary library or product owner.
- Zero-day exploitation. The Log4j2 vulnerability is relatively easy to access and exploit through numerous vectors. While Proof of Concept code was immediately made available, what happened next was predictable: widespread exploitation of Web and Gaming services followed by more targeted PoCs released targeting different implementations. Defenders simply did not have time to respond given the scope of vulnerable systems.
We have now learned many lessons from this Internet-wide event, including the significance of the modern controls and processes. Now what?
First, prioritize remediation through dynamic visibility. It’s vital to understand your current landscape. Not through sampling or snapshots, but now. Discovering, observing, and controlling your application relationships and dependencies across your entire IT estate is an important step in defending against CVE exploits like Log4j; breaches including ransomware and insider threats; as well as mistakes and neglect. This is the purpose and promise of Application Relationship Management (ARM).
For example, you have 10,000 vulnerable servers with different sets of software interdependencies and complexities to remediate. Where do you start?
Many modern regulatory frameworks have begun to recognize the importance of prioritizing Important Business Services (the UK PRA) and Critical Business Functions (FFIEC in the USA). The vArmour Application Controller, the heart of vArmour’s platform, allows you to map the scope and dependencies of your applications with your inventory of vulnerable systems, to provide a prioritized list for remediation. In practical terms, utilizing the Application Controller’s labeling function (with input from a vulnerability management system integration, CSV file, or API-based automation code) enables you to label vulnerable systems and issue advanced searches or produce reports showing the list of servers that are dependencies of systems which, in turn, map to a critical application (the ‘App Name’ label); or to systems labeled by tier or regulatory status. ARM connects application maps to metadata such as vulnerability information to streamline the prioritization of your remediations.
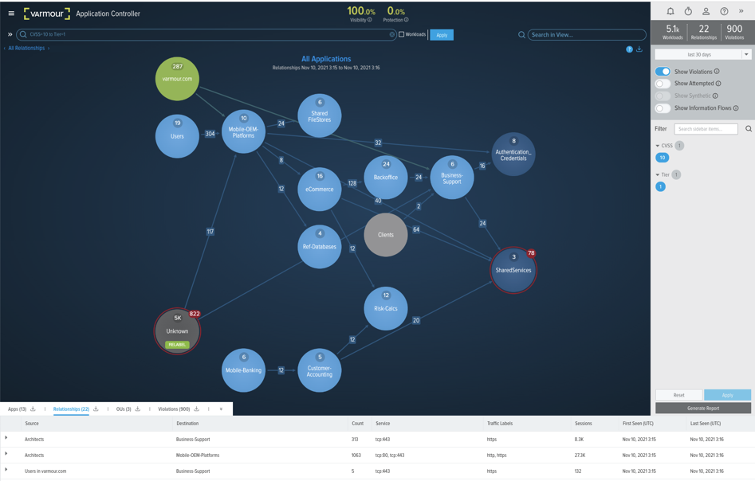
Exhibit 1: Map of dependencies between Tier 1 systems & systems with detected CVSS = 10.
Actionable Observability – Detecting Attempted Exploits at Scale
During a massive remediation effort, the risk of attempted exploits going undetected over the course of the assessment and mitigation process persists. vArmour Application Controller allows you to establish a baseline of observed and expected behavior (once again focusing first upon Critical Business Functions based upon business tier or application membership) and use it to identify and notify you when deviations occur. This approach allows you to manage your risk by responding to new and unexpected communications paths which could represent an attempt at lateral exploitation until the vulnerability has been remediated.
It is still early days. Many organizations are still experiencing new vulnerability notifications and are working hard to mop up the mess. It is important for us to learn some of the lessons taught about the complexity of our software deployments and the tools we need to mitigate and manage risk, particularly in the most complex environments.




