A Look Inside the PrintNightmare - Protecting Against Zero-Day Attacks

As the sophistication, speed, and frequency of cyber attacks grow it is critical to view security from the perspective of the dynamic perimeter. Understanding threats, and responding to them in virtual real time is critical to securing assets from mainframes to micro-services.
At vArmour, we have seen an uptick in Zero-day attacks, exploiting vulnerabilities in unpatched systems. With the size and scale of the enterprises we have worked with, we know it can be hard to always stay up-to-date, but that shouldn’t compromise your security posture.
One of the attacks we spotted recently was a Zero-day exploit: CVE-2021-1675, better known as PrintNightmare (catchy, I know). PrintNightmare is an EoP (Elevation of Privilege) hole in pretty much every supported Windows version, all the way from Windows 7 SP1 to Server 2019. If you had compromised user credentials for someone in your workforce, this exploit would allow the hacker to elevate their privileges and get access to a lot more than that user was privileged for to potentially install programs, modify data and create new accounts with full admin rights.
Here is how we help.
vArmour dynamically maps enterprise environments, applications, infrastructure, and the users that access them. We do this in real time, allowing you to see exactly what is happening within your environment.
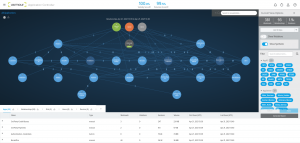
We then create intelligent policies that control the user access or alert to baseline deviations from normal business operations, sending them directly to you SOC via Splunk, or alerting the security team in real time.
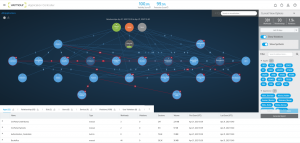
vArmour identifies users, what they have access to, and how much of these privileges they are actually using, building a pattern of relationships and behaviors that is considered acceptable.
In the case of PrintNightmare: We would spot Tim from HR, who typically accesses the application responsible for Payroll and Employee records. Furthermore, we would see Tim now accessing Finance applications, accessing the servers that contain R&D files, and start pinging the data out to an unknown internet device that isn’t a part of your CMDB.
Alerts would be sent within seconds, letting Security Operations teams know, as well as the Vulnerability team. We would then generate an executive-level Summary Report on the user and the unexpected behavior, correlating all the relevant information, allowing your teams to respond quickly.
Attacks like this are already common, and will continue to increase. As the Washington Post reported, cyber attacks cost organizations over $1 Trillion in 2020. A fundamentally different approach that makes the perimeter and your security policies dynamic is the critical path to reducing the cyber burden and keeping your organization, your employees, your IP, and your customer data safe.




