vArmour Reveals Hidden Data Flows Through Middleware for Enterprises

vArmour Data Flows Module solves existing blind spots in understanding and controlling multi-hop application relationships
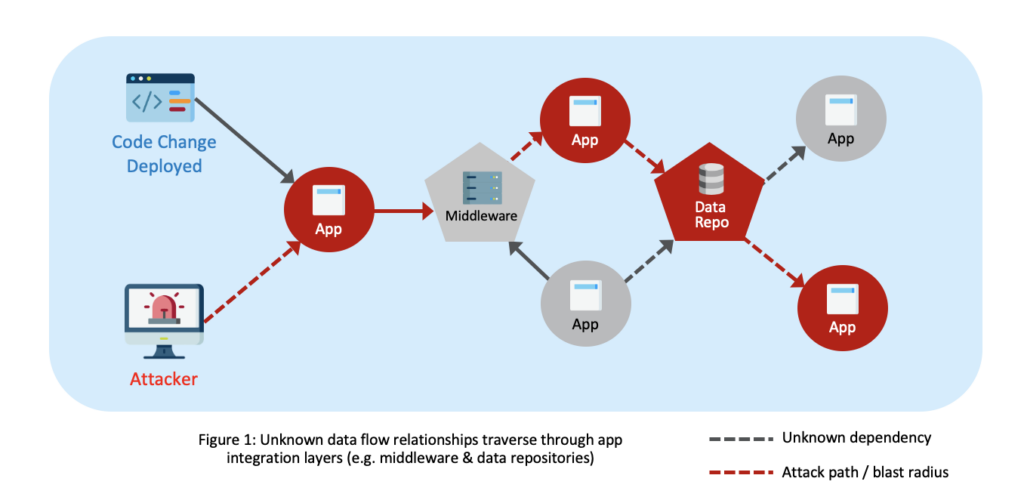
Modern enterprises are all digital-first organizations, but that does not make them simple to run. Digital-first requires highly interdependent applications and data. Some are modern cloud-native applications and others are legacy dinosaur applications the business will never survive without. Either way, the applications are more complex and distributed than ever before and enterprises don’t understand the blast radius of incidents nor the greater risks they face.
An important role in interconnecting critical applications and facilitating asynchronous data transfers is played by middleware systems like messaging queues (MQs) and FTP servers. But as we’ve explored in two previous blogs— How Resiliency Starts with Visibility and The Black Hole of Middleware Complexity—middleware can cause a major blind spot in application dependencies and data flows that create disruptive and costly cyber resiliency and security challenges for many enterprises.
Introducing vArmour Data Flows Module
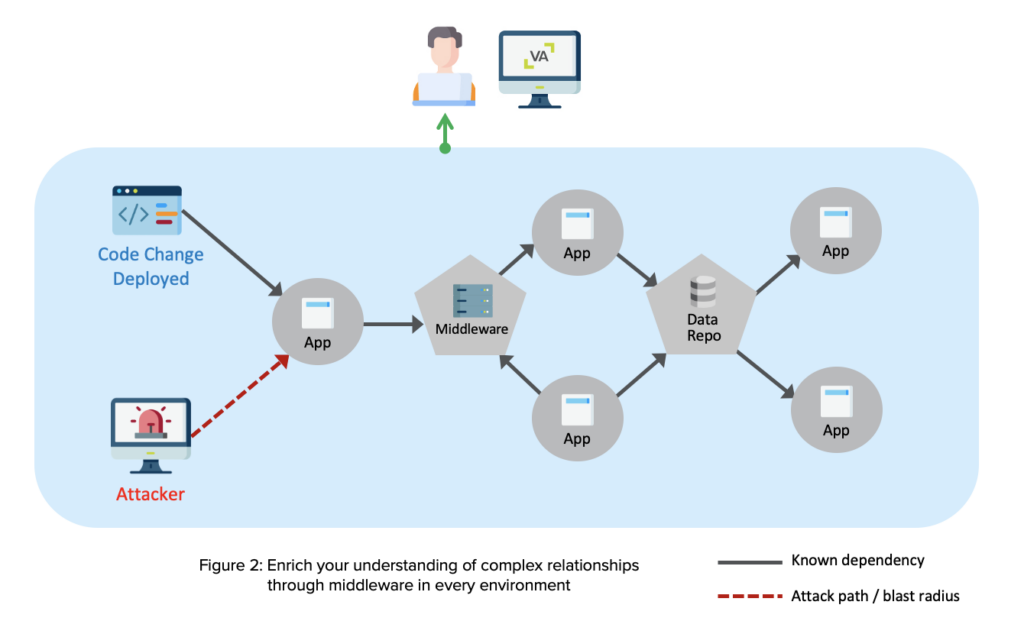
Now, there’s a new and unique solution that solves this blind spot in middleware. vArmour is pleased to announce the general availability of a major new capability to help customers to discover, visualize, and understand the data flow relationships between their applications through middleware. This capability fills a big gap for customers.
“Without understanding the upstream and downstream from middleware, we would not get an accurate view of the end-to-end flow,” said a customer, the Managing Director of Technology, Major U.S. Bank.
vArmour provides automated, continuous discovery and end-to-end view of multi-hop application relationships and data flows through middleware with important positive business outcomes:
- Reduce cyber risk: Reveal the hidden attack paths and data flow relationships attackers use to traverse networks
- Improve cyber resiliency: Ensure recovery time objectives for interdependent applications to avoid outages
- Provide regulatory assurance: Automated discovery of data flows to comply with new and emerging mandates
Summary of Data Flows capabilities
Discover Data Flows Continuously
- Continuously discover data flows between all assets and workloads through middleware like IBM MQ and FTP servers with a centralized ML-based relationship mapping engine
Visualize Data Flow Relationships Between Applications
- Visualize and understand multi-hop dependencies and data flows through middleware
Leverage a Single Relationship-Based View
- Leverage a single application-centric and relationship-based view across enterprise IT for understanding your risk, attack surface, and blast radius
Use API-Based Integrations For Middleware
- Integrate easily via a standard API connector framework with common sources of business, IT, and security data, including middleware platforms like IBM MQ and FTP servers
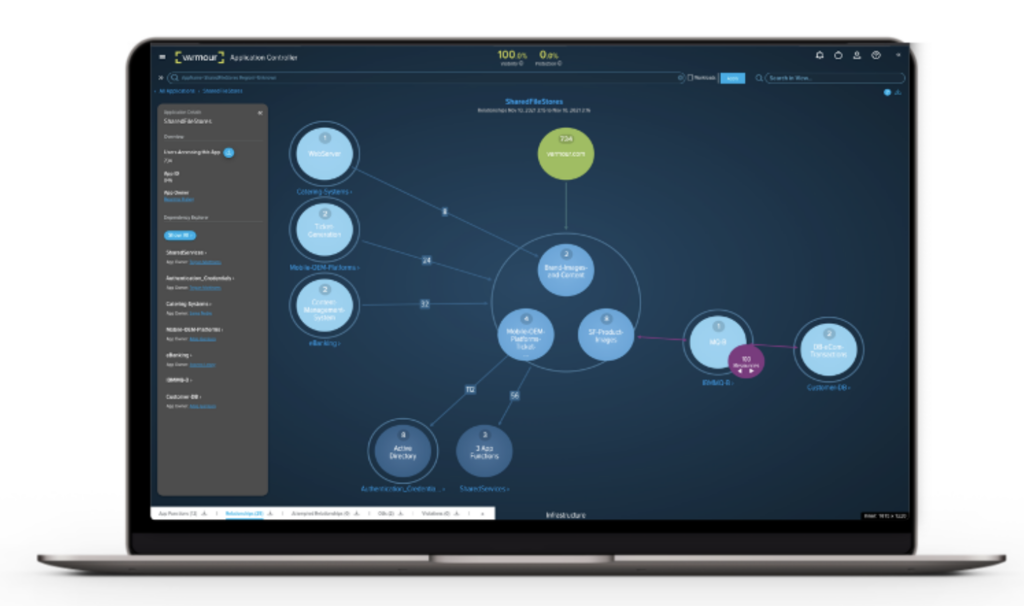
Figure 3: Discover, observe and control the relationships of applications, users, devices and data
vArmour’s new Data Flows capability is now generally available as subscription software or as part of vArmour’s SaaS-based service, Relationship Cloud.
To learn more, please be sure to see these resources:
Follow author Andrew Hendry on Twitter @awhendry




