Decoding DORA ICT Risk Management Requirements: Step 2 - Mapping your Business Functions and their Dependencies

Today we will dive into the essence of delivering Operational Resilience within complex digital organizations — establishing an accurate inventory of the dependencies required to deliver your business functions in order to ensure operational and cyber resilience.
So far in the DORA ICT Risk Management workflow we have focused on collecting the information allowing us to understand our environment, our ICT assets, and their relationships and dependencies.
At Step 2, we are required to organize that information in the context of our business functions (in particular our Critical Business Functions and Important Business Services) so that we can understand the scope of those functions, their dependencies, and the risks associated with them.
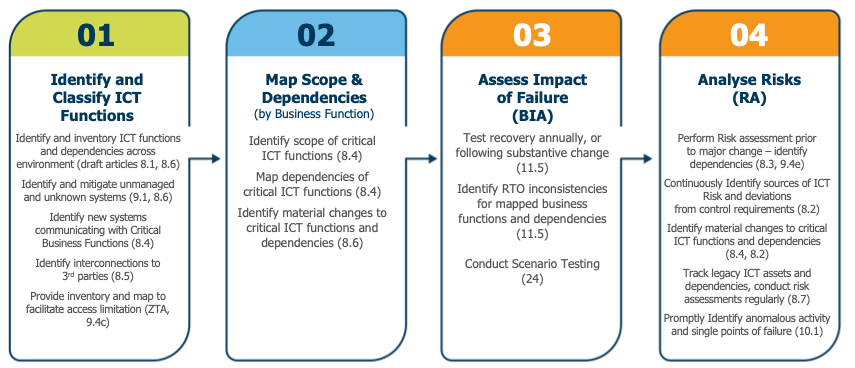
Figure 1: The steps in the ICT Risk Management workflow as defined by the DORA articles (including brief summaries)
Why is an Inventory and Map Important?
One of the greatest challenges caused by digital transformation is the complexity and rate of change within the services required to deliver a business function. Increasingly, inventories need to be dynamic in order to keep up with the rapidly changing digital environment, but they also need to consider the interdependencies between systems which have become distributed, disparate, and decomposed as we move towards services oriented and microservices architectures. The inventory required to deliver Operational Resilience in a digital organization is dynamic and understands interdependencies across the entire organization and its digital estate — essentially a data-driven automated map to provide ground truth.
vArmour’s Map delivers several benefits underpinning an organization’s operational excellence. In 2019 the European Banking Authority’s ‘Guidelines on ICT and Security Risk Management’ broke this down really nicely:
- The ability to avoid operational incidents to enable a proper configuration and change management program (article 53).
- The ability to recover and respond to security and operational incidents (article 54).
- The ability to assess impact and risk by analysing exposure to severe business disruptions and assessing their potential impacts (article 78).
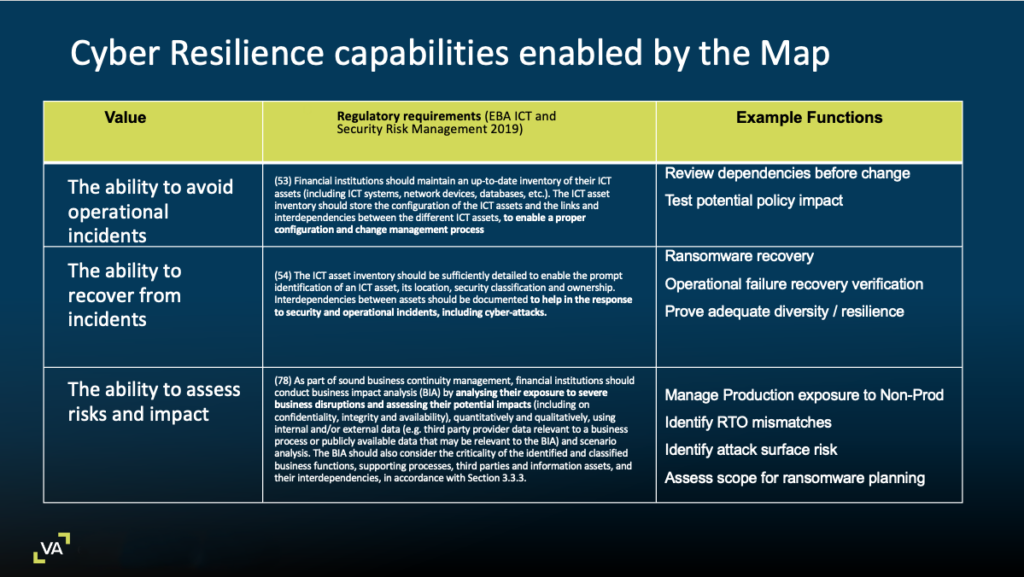
Figure 2: Alignment between the vArmour Map capabilities and European Banking Authority’s ‘Guidelines on ICT and Security Risk Management’
The DORA Requirements
Requirement 1: Identify Scope and Map Dependencies of Critical Business Functions
Article 8.4
Financial entities shall identify all information assets and ICT assets, including those on remote sites, network resources and hardware equipment, and shall map those considered critical. They shall map the configuration of the information assets and ICT assets and the links and interdependencies between the different information assets and ICT assets.
DORA focuses on the Resilience of Critical and Important business functions. In order to deliver the operational and cyber precision required to be resilient, the ICT Risk Management pillar requires organizations to map their critical business functions, the components and interdependencies across their entire environment (including third party dependencies). The map then forms the basis for operational processes and risk management, allowing organizations the necessary situational awareness to make good decisions.
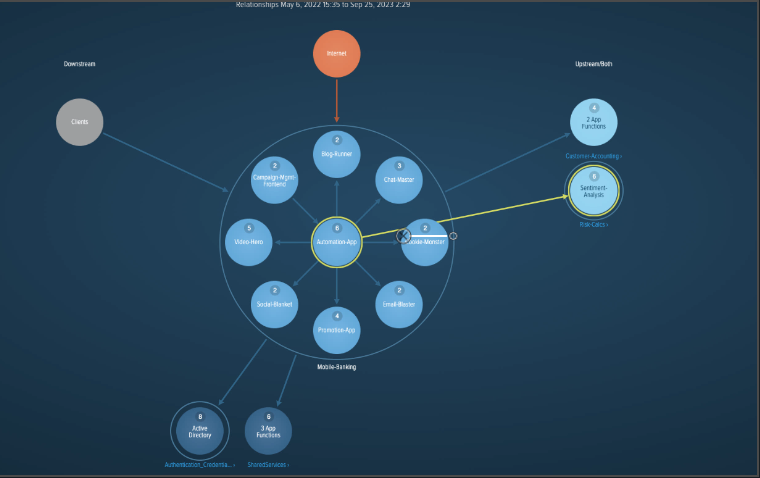
Figure 3: Screenshot of the vArmour Map showing all application functions and dependencies for a selected critical application
Requirement 2: Identify Material Changes to Scope and Dependencies of Critical Business Functions
Article 8.6
For the purposes of paragraphs 1, 4 and 5, financial entities shall maintain relevant inventories and update them periodically and every time any major change as referred to in paragraph 3 occurs.
Article 8.3
Financial entities, other than microenterprises, shall perform a risk assessment upon each major change in the network and information system infrastructure, in the processes or procedures affecting their ICT supported business functions, information assets or ICT assets.
The map needs to be maintained to be accurate and useful. DORA specifically requires it to be updated after major changes affecting any of the component systems. Across even moderately complex or dynamic environments, automation is required to ensure the inventory remains accurate and complete.
In addition to this capability, vArmour Relationship Cloud allows organizations to generate behavioral baselines which will issue alerts where material changes to behavior are identified. This can enable organizations to validate that change processes are followed, and to identify where anomalous conditions occur.
Conclusion – A Contextual Map Enables you to Focus on your Critical Business Functions
Operational Resilience requires organizations to focus on their Critical Business Functions. By collecting information about the entire environment and contextualizing around business functions, vArmour Relationship Cloud delivers accurate and current situational awareness to the teams operating each function. This capability facilitates focused and precise risk management, operational excellence, and immediate situational awareness when material changes occur.
By taking an automated data driven approach, vArmour allows organizations to consider risk across their entire digital estate while focusing particularly on their Critical Business Functions. In our next article in this series we will explore how the Map underpins business impact analysis (BIA), scenario testing, and risk assessments as required by DORA.
Video Demo
See how the vArmour Relationship Cloud simplifies and accelerates Step 2 in the DORA ICT Risk Management journey here.




