Simplify securing your organization's attack surface.
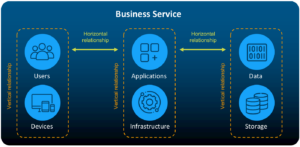
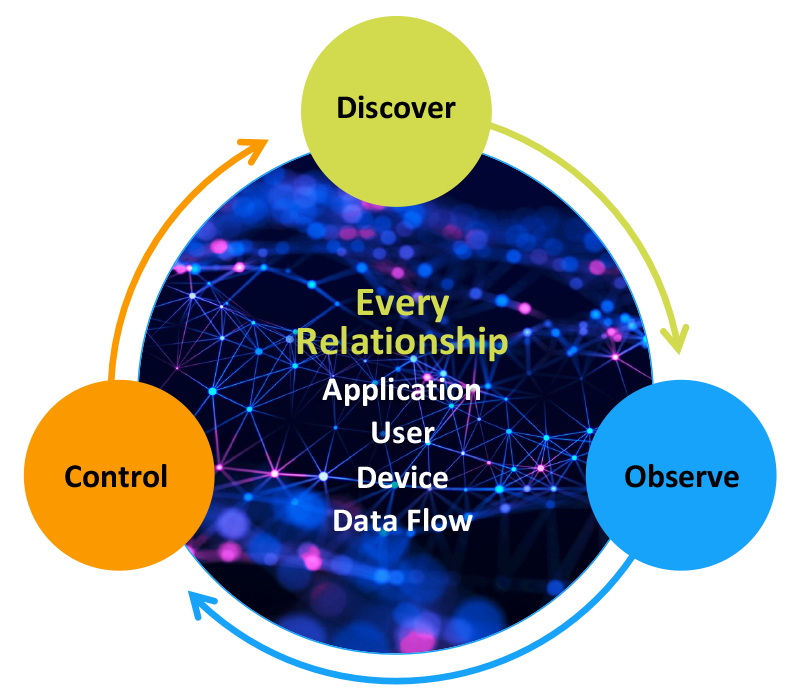
vArmour manages the cyber attack surface through discovering, observing and controlling the relationships and dependencies of applications, users, devices and data. With vArmour, enterprises can manage their cyber asset attack surface, and take the next step in securing them:
- Continuously discover the entire estate of application assets, relationships, and dependencies
- Observe and control the exposure points and propagation vectors of ransomware and other cyber risks to prevent attacks and reduce cyber risk
- Ensure resiliency of applications through continuous observation of relationships and change impact
- Isolate, segment, and control critical applications and business systems leveraging existing controls
Learn why business context is critical to understanding your attack surface.