FFIEC Risk & Relationship Series: Best Practices of Business Impact Analysis

In this session, we will finalize the discussion on the Business Continuity Management (BCM) process and the Business Impact Analysis (BIA). This includes looking at impact assessments and risk assessments, and a deeper dive into resiliency requirements and the implementation of a successful BCM program.
In the BIA process, we first identified critical functions and their interdependencies, as explained in the previous blog.
We will also explore how an Application Relationship Management solution, such as the vArmour Application Controller, allows you to automate each aspect of the technical BIA process – establishing the scope of your critical business function, identifying its dependencies and evaluating whether the recovery capabilities of the end-to-end system allow the organization to meet its goals and obligations. Watch the webinar to learn more and view the full demonstration, or read the excerpt below.
Watch the full webinar to learn more:
Exploring Business Impact Analysis
The impact assessment stage of the BIA is the function that prioritizes and assesses the ability of critical functions to be recovered. Once that is complete, the risk assessment enables an organization to model the risk or likelihood for a failure or event to occur. Both of these functions were historically managed as manual, periodic pieces of work. However, as we move towards the requirement for continuous resilience, we will explore the benefits of automation and application relationship management to continuously assess risk.
Impact Assessment
Failures are inevitable, and will eventually occur at the worst possible moment. As risk managers, it is incumbent upon us to plan diligently for what will occur and what the impact will be when that failure occurs. This is where the work to complete the impact assessment comes in.
Impact assessment can be assisted by considering resilience in the design and testing process. It is how you can model the impact of disruption to your interdependencies of your critical functions.
Steps to Assessing Impact
Through the impact assessment process, managers should evaluate the potential impact of disruptive events, extrapolating to operational, financial, and reputational impacts. Managers should also establish recovery objectives after determining a disruption’s impact. Common measurements include recovery point objective (RPO), recovery time objective (RTO), and maximum tolerable downtime (MTD).
Establish Business Requirements: Determining MTD of a service allows you to establish the recovery time capabilities you need for your critical function and it’s dependencies. The Security and Exchange Commission (SEC) recommendations for MTD systemically critical functions (for example, settlements and reporting functions) are an hour, but this will depend upon your business requirements. In particular, think about the tolerance when a failure occurs at the worst possible moment, e.g. a few minutes before market close, or during a period of high market volatility.
Consider the Capabilities of Modeling System: The second thing you need to consider is how much data can you afford to lose? Data can be recovered using multiple different strategies, with persistent storage or recovery of data from an interdependent source.
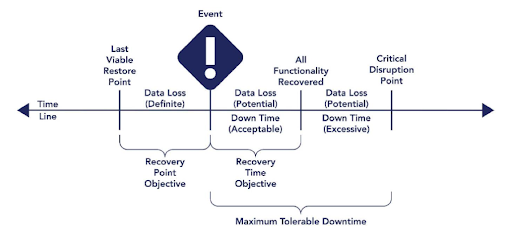
Establish a Timeline of Failure: The time between the last viable restore point and the failure event is the period of data loss and you must consider this in your impact assessment. If that period is too long, you will have to determine other ways to recover your data.
RTO is the period after the event occurs where we need to recover our application and business function within. During this period of recovery, you should consider what happens to any data that may be generated upstream or downstream systems.
What happens if your ability to recover doesn’t match your MTD? Once you complete this analysis, you will need to consider what happens if your ability to recover does not match your MTD. If this is the case, you can mitigate by refactoring your application or you can accept the risk associated with it. Once you’ve done this, you need to document this so you can model the impact across more complex sets of interdependencies and test your system on a periodic basis to ensure it continues to behave in the expected fashion.
Once you have done this, you need to understand the same for the interdependencies of that function. Establishing consistency of RTOs for a business function and it’s interdependencies is a particularly challenging problem in complex financial environments and it is a key capability of systems that provide Application Relationship Management.
In the demo, we demonstrate assessing RTOs across a system and its interdependencies in an automated way using Application Relationship Management.
Resiliency Requirements in Impact Assessment
Failure is inevitable, yet resilient systems allow you to recover automatically. Furthermore, when you are considering resilience and reducing the impact of failure, you need to look at application design patterns. This is the essence of the new focus on resilience, as systematically resilient architectures are incredibly important.
Reduce Scope of Failure with Microservices Architecture: Anti-fragile and decoupled design patterns, or microservices architecture, reduce the scope of failure and recovery. Microservices architectures can be used to reduce the scope of failure of components, but at the cost of increasing the scope of interdependence. Thus, as you move towards this microservices architecture, you need to further understand interdependencies.
Embed Failure within your Operational Model: Deliberately inducing failure, using Chaos Monkey for example, then becomes a daily part of the operational lifecycle and is no longer an event to be feared.
Continuously Assess Risk: Because Application Relationship Management is data driven and automatic, you can rest assured changes in your interdependencies will be automatically identified, so your BIA remains continuously correct.
Risk Assessment Process
Now you have the processes and tools in place to provide a continuous BIA, but that isn’t the end of the story. In the overall calculation of risk, we have considered the business impact, but now you must evaluate the likelihood of a disruption occurring, known as the risk assessment. Examples of the types of risk that can be included are the attack surface of the system, security vulnerabilities and operational metrics. Cyber risk is called out as an important part of the risk assessment also. Once again, Application Relationship Management allows you to execute your risk assessment with this sort of information embedded into your views of your critical business functions.
The Implementation
The FFIEC booklet speaks about the implementation of the BCM program, and different strategies that should be built in. It talks about a number of topics we have addressed here including resilience as opposed to recovery from an event. This requires that resilience is built into application architectures, infrastructure solutions and into the operational process. Failures and the scope of failures need to be limited. For instance, when you have dependencies on a third party, i.e. cloud provider, it is important for an organization to reduce the scope of failure to a single point of dependency as much as possible. Once again, Application Relationship management can provide you with a current view of infrastructure dependencies, for example on a single cloud datacenter.
Finally, in the preparation for events, you have to ensure you have the tooling, the plans, the resilient application architectures and the training and practice in place so your recovery will be seamless and you will be well prepared. It is imperative that you keep your BIA and risk assessments up to date.
In the coming weeks, we will have more in depth sessions on the FFIEC Cyber Assessment (CAT) Tool and the cyber control requirements for institutions within Financial Services. To learn more about the changing focus of Business Impact Analysis and Risk Assessments, view the full session on demand here.
The Risk and Relationship Series Agenda
Over the coming weeks, we will step through several aspects of the FFIEC’s requirements, and also explore their global counterpart’s views. This series will also include topic-relevant demonstrations of a continuous data-driven approach solution called Application Relationship Management, using the vArmour Application Controller.
The series topics are as follows:
- FFIEC IT Risk Management
- Business Continuity Management: Governance & Risk Management
- Business Continuity Management: Assessing Impact
- Assessing Cyber Risk with the Cyber Assessment Tool (CAT)
- Controls – Network Controls and How to Build Dynamic Inventory
- Controls – Change Management, Assurance and Testing
- Controls – Remote Access
- Controls – Cloud Computing
- Security in a Cloud Computing Environment
If there are any aspects of Operational or Cyber Resilience you would like to see covered in this series, please get in touch with me at vcomm@varmour.com.





