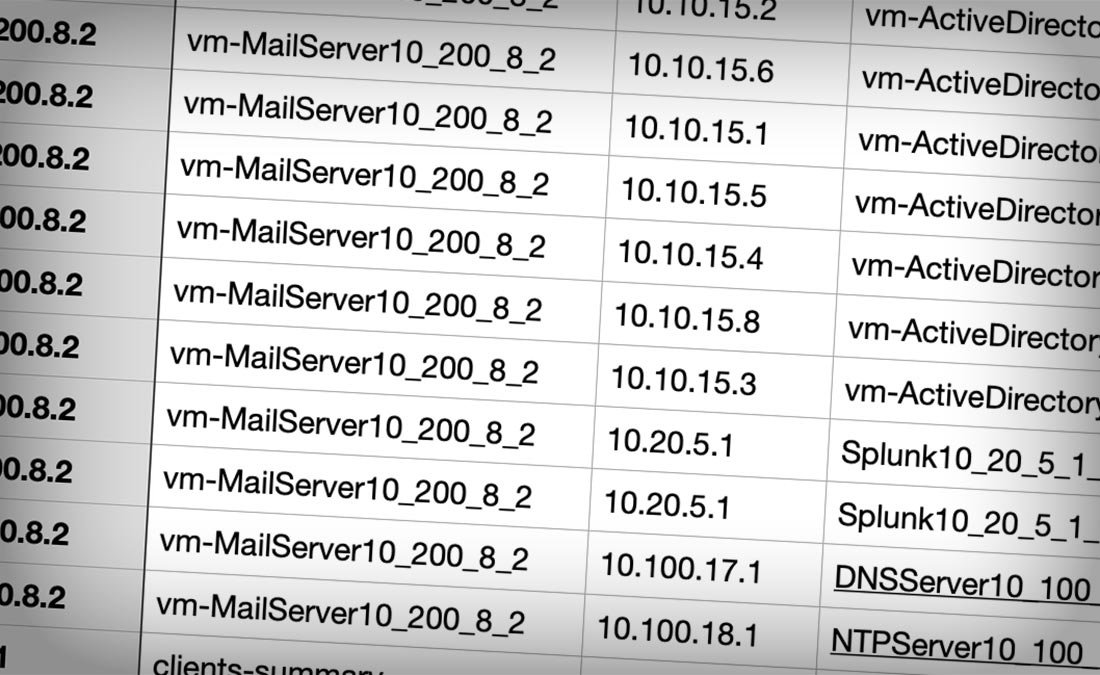
See how your applications behave and get to ground truth—fast.
Your application stacks span a mix of new and old — vArmour takes native telemetry and transforms it into a single picture, from lateral movement between individual workloads, to data moving between regions and clouds. vArmour visualized mapping is like Google Earth for your digital business.